Imagine this: your business is thriving—until a cyber incident hits. Systems crash, data leaks, and customer trust vanishes.
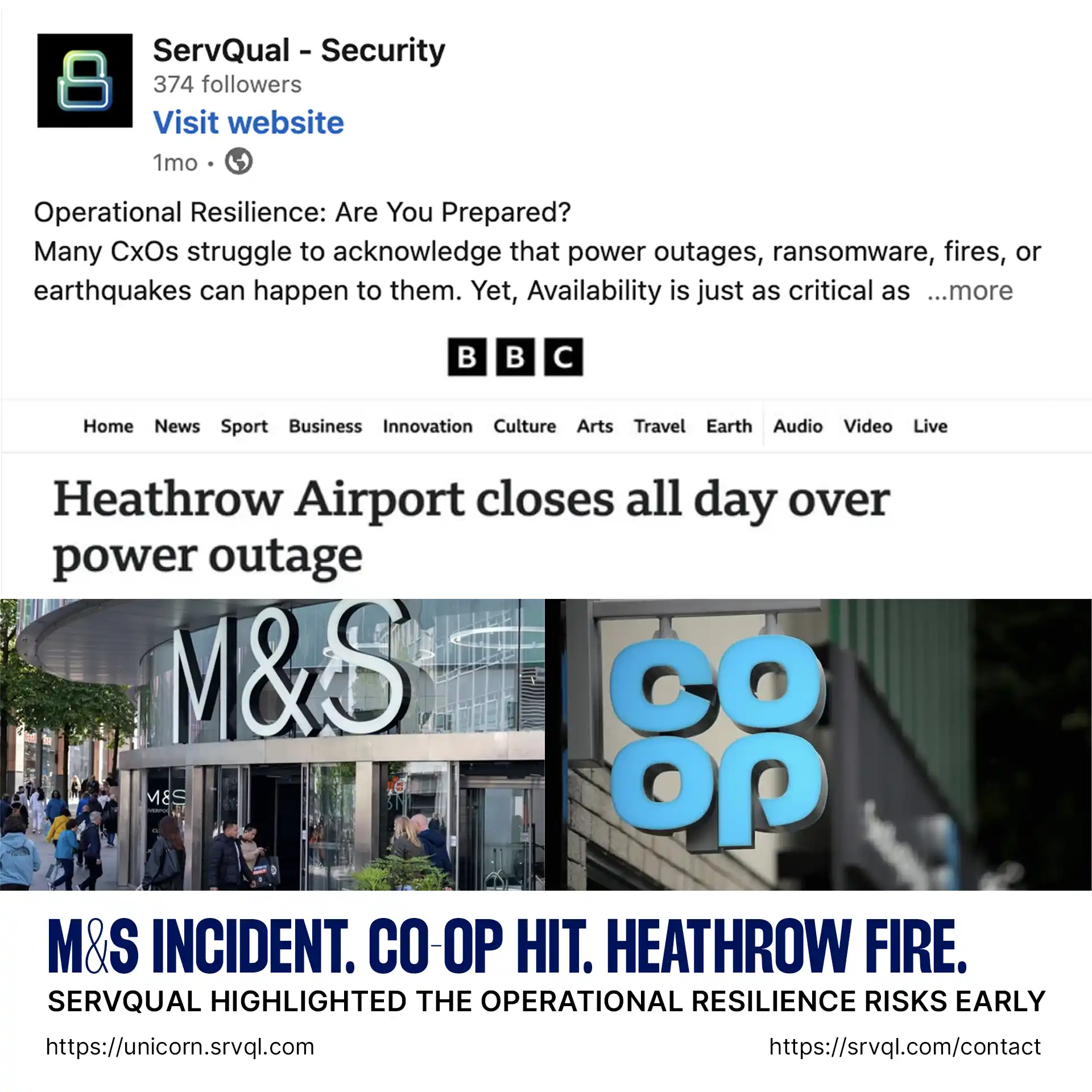
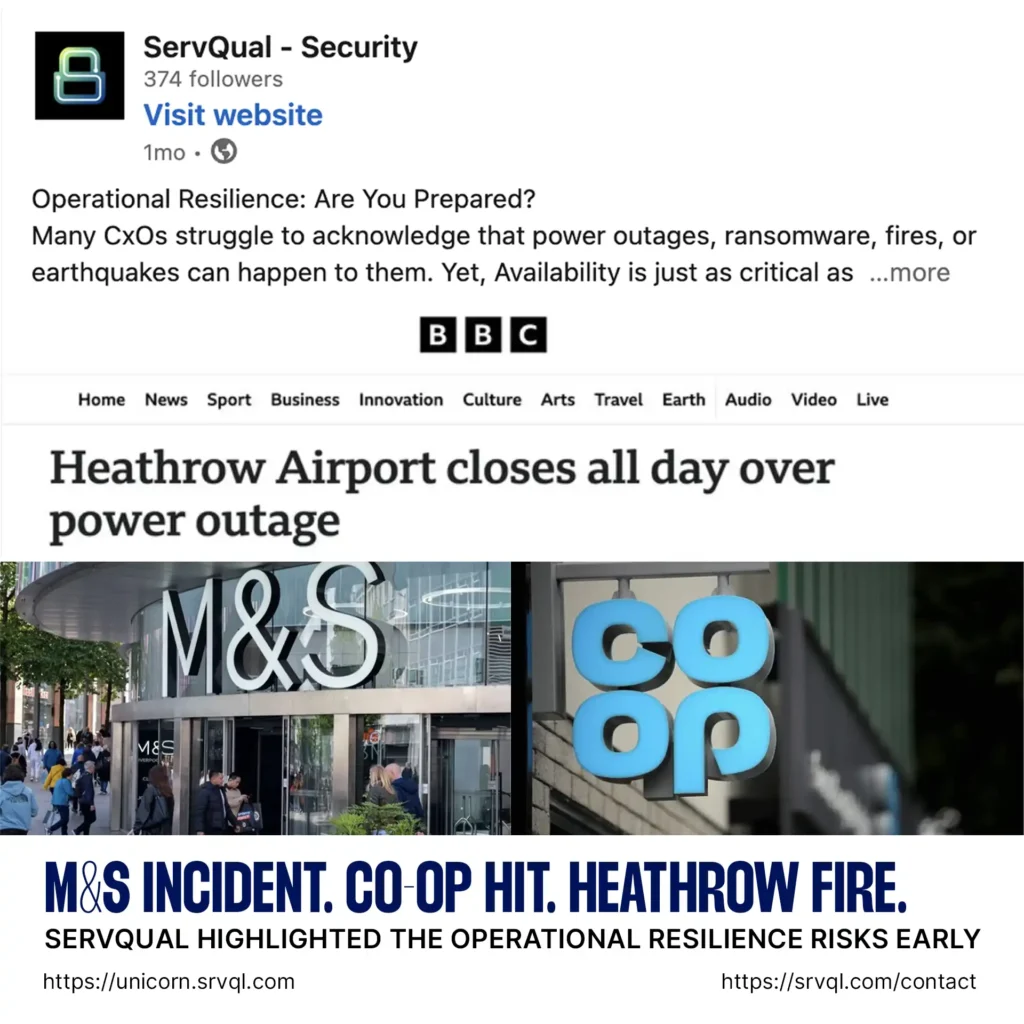
This is exactly what happened to Marks & Spencer (M&S) and Co-op in recent high-profile cyber incidents. And while Heathrow Airport’s massive outage wasn’t caused by hackers, it reminded us how quickly operational chaos can spread without resilience planning.
Even the biggest brands are learning the hard way: cybersecurity alone isn’t enough. Today, operational resilience is essential. The rise in ransomware and sophisticated threats has made preparedness non-negotiable.
According to IBM’s 2024 Cost of a Data Breach Report, the average breach now costs $4.88 million, with response time often being the deciding factor between recovery and reputational damage.
In this blog, we’ll explore key cyber incident response strategies, real-world lessons, and how ServQual helps organizations strengthen their security and resilience
What is Cyber Incident Response?
Cyber incident response is a structured approach to handling and mitigating the aftermath of a cyberattack. This includes detecting the breach, analyzing the impact, containing it, eradicating the threat, and recovering operations. It often involves a blend of human expertise and automated tooling.
When aligned with operational resilience, it ensures minimal disruption to your core services during and after an incident.
Why Operational Resilience Needs Robust Incident Response
Operational resilience is the ability of an organization to continue delivering services through disruption. A cyberattack, if not managed efficiently, can paralyze operations damaging trust, finances, and compliance posture.
Key reasons to integrate cybersecurity into your operational resilience framework:
- Prevent prolonged downtime
- Avoid legal penalties (GDPR, HIPAA, etc.)
- Safeguard customer data
- Maintain stakeholder trust
- Strengthen compliance posture (ISO 27001, SOC 2, etc.)
Real Incidents That Reshaped Cyber Response
Marks & Spencer Ransomware Attack (2025)
In April 2025, UK retailer Marks & Spencer (M&S) suffered a significant ransomware attack attributed to the Scattered Spider group, which utilized the DragonForce malware. The attack led to widespread operational disruptions, including suspended online orders, malfunctioning contactless payments, and empty shelves in stores. The breach reportedly began as early as February, with attackers stealing sensitive Active Directory data before deploying the ransomware. M&S collaborated with cybersecurity firms like CrowdStrike and Microsoft to mitigate the impact.
Co-op Cyberattack Attempt (2025)
Shortly after the M&S incident, the Co-op Group experienced an attempted cyberattack, leading to the shutdown of parts of its IT infrastructure. While stores and services continued operating normally, the incident highlighted the growing threat of cyberattacks on major retailers and the importance of proactive cybersecurity measures
Heathrow Airport Power Outage (March 2025)
On March 21, 2025, a catastrophic fire at the North Hyde electrical substation in Hayes, west London, led to a significant power outage at Heathrow Airport. The blaze caused the cancellation of over 1,300 flights and disrupted travel plans for hundreds of thousands of passengers. Despite having backup power systems, the airport’s high energy demands posed challenges in maintaining operations. The incident underscored the critical importance of infrastructure resilience and the need for robust contingency planning.
Colonial Pipeline Ransomware Attack (2021)
One of the most disruptive attacks in U.S. critical infrastructure, the Colonial Pipeline ransomware incident led to widespread fuel shortages. The root cause? Inadequate segmentation and lack of rapid containment protocols.
Nvidia Hack (2022)
The Nvidia cyberattack by Lapsus$ exposed employee credentials and source code underscoring the need for insider threat detection and breach containment.

Effective Cyber Incident Response Strategies
Establish an Incident Response Plan (IRP)
Formal documentation defining roles, response phases, escalation protocols, and communication guidelines.
Automate Threat Detection & Response
Use AI-driven tools and SIEM platforms to reduce response time.
Simulated attacks help your team build muscle memory for real threats.
Enable Endpoint Detection and Response (EDR)
Monitor endpoints for anomalous behavior in real-time.
Adopt a Zero Trust Architecture
Assume breach and verify everything internally and externally.
Integrate Response with Business Continuity
Your IRP must align with broader continuity and disaster recovery efforts.
Partner with an Expert Cybersecurity Provider
Partnering with ServQual ensures bridging the gap between business leadership and security engineering, overall security awareness across the board, scalability and preparedness to respond to adverse incidents.
Companies That Excel at Cyber Response
Effective incident response isn’t built overnight, it’s driven by deep expertise, automation, and real-time intelligence. Here are five companies recognized for their excellence in this field:
- ServQual – ServQual is a cybersecurity services company that specializes in incident response, operational resilience, compliance readiness, and security automation tailored for IT service providers and SaaS businesses.
- CrowdStrike – Known for endpoint detection and threat intelligence.
- Mandiant (now part of Google Cloud) – Specializes in post-breach forensics and nation-state threat response.
- Palo Alto Networks – Delivers AI-enhanced threat prevention across networks and clouds.
- Rapid7 – Provides cloud-native security operations and risk management solutions.
“Operational resilience is no longer just about surviving disruptions—it’s about adapting in real time to the evolving risks posed by Generative AI.”
Final Thoughts
Cyber threats are growing in complexity, but your defense strategy doesn’t have to. By learning from past incidents and leveraging modern solutions like ServQual SUSAN, you can transform your organization’s resilience and ensure every incident becomes an opportunity to strengthen—not break—your system.
Explore ServQual’s cybersecurity platform SUSAN to get a free Gen AI Security & Compliance assessment today.
We’re constantly sharing real-time updates and insights on recent cyberattacks, infrastructure outages, and regulatory changes on our ServQual LinkedIn page. For example, we recently covered the Heathrow Airport power outage in March that led to the cancellation of over 1,300 flights due to a major substation fire, highlighting how even non-cyber incidents can disrupt operational continuity.
Contact us to stay ahead of evolving threats and best practices in resilience.
FAQs
What is operational resilience in cybersecurity?
Operational resilience refers to an organization’s ability to withstand, adapt to, and recover from cyber incidents—ensuring critical services continue with minimal disruption.
How often should we update our incident response plan (IRP)?
Your IRP should be updated at least twice a year, and after any major incident, regulatory change, or internal restructuring.
Is incident response only necessary for large enterprises?
Not at all. In fact, SMBs and mid-sized SaaS firms are frequent targets due to having fewer cybersecurity defenses in place.
Can ServQual support compliance requirements like GDPR or ISO 27001?
Yes, ServQual’s resilience-first approach helps meet GDPR, ISO 27001, SOC 2, and other critical compliance frameworks.
Are ServQual’s solutions affordable for startups and small businesses?
Absolutely. Our modular and scalable pricing ensures essential cyber resilience tools are accessible without heavy upfront investment.